|
General Linux based Firewalls are either Standard Server Hardware or a Special Design Hardware appliances running Linux operating system specifically configured to provide border security on a network. Operational Functions Secure connectivity On Standard Hardware based Linux Firewalls, HyperManage can provide Server Console Access via HyperNode IP-KVM port. The IP-KVM server connection of the HyperNode allows to remote a Linux-Based Server access by physically remoting its Keyboard, Video, and Mouse and operate them from a different computer normally located in a remote location. Furthermore the HyperNode based IP-KVM System does not only allows full Server Remote Access down to the BIOS level, it also provides, on Standard Server Hardware systems, remote media mapping so that a block type device like a disk image physically located on the remote computer can be made available on the Controlled Server. LAN based services on a Linux Server based Firewall can also be accessed in full security through the HyperNode LAN port, that provides a secure IP tunnel right up to the firewall software. This gives access to different services like configuration services available via an http/https connection. Such connection can be used in full security via the HyperManage virtual VPN system without necessarily using the Server Console KVM access feature for such type of access or the Serial based access. Serial port based services on the Linux Server based Firewall can also be accessed in full security through the HyperNode Serial Port connection. HyperManage through the HyperClient provides full virtual serial port remote support on the accessing computer. The virtual remote serial port is mapped to the physical serial port on the HyperNode through a secure IP tunnel. This allows a direct connection to the serial port of some Linux firewall where certain software features can be mapped through such interface. In some Linux based Firewall, the emergency access port is mapped through a special function serial port: consequently it is very important to be able to physically remote its access. Operational Condition: The Server Console access based on the IP-KVM interface as well as the Firewall Serial Console access do not relay on the Server's LAN access being active and operational so, as far as the HyperNode can connect to the HyperServer via either its standard LAN access, via an alternative or Out of band LAN access (via a USB 3G PEN for instance) then the access to the Server's through such ports is guaranteed. On the other hand if something goes wrong to the Server's LAN connectivity due to the primary LAN failure or a Firewall LAN misconfiguration then the LAN based access will become inoperative. 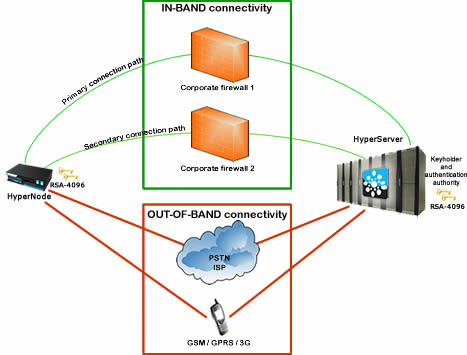 Automatic login procedure The HyperManage platform can be set up to centrally store all device credentials, in order to avoid to share them with all the various people that might need to access the such devices: this is a more efficient way to manage security in accessing remote devices especially when “free-lance” technicians are employed maybe through an outsourcing contract. When any technician ends his job and he is not supposed to perform further accesses to some systems, to avoid further connections, his/her account or access scheme can be centrally disabled or reconfigured without worrying about having distributed any specific device access credentials to third parties. On an IP-KVM based console access, the credentials necessary to log into the system with the right privilege level can be automatically “typed-in” by the HyperNode by a keyboard shortcut user request: this way the technician logs in into the Windows Server based firewall with the privilege level predefined by the HyperManage system administrators without ever having any knowledge of the Server Passwords. On Linux-Based FireWalls accessed via specific services either provided through a serial port connection (terminal type connections) on a LAN based port connection (based normally on ssh or telnet protocols or others) , custom login scripts can be easily developed to be downloaded to the relevant HyperNodes and executed on a specific LAN service access request, to provide automatic login to potentially every available service to the specific authorized users. Remote power control HyperManage external proprietary PDUs (Power Distribution Unit) connected to a specific HyperNode, allow to remotely control the mains power of Linux-Based Firewalls. This is a further essential tool that can enable the technician to perform a cold boot on a firewall, being able to follow, via the IP-KVM based console connection, or the Serial port connection all the boot process, with the possibility to intervene during such process, including entering the BIOS level configuration procedures in the case of KVM or reloading factory configuration or alternative firmware of Serial port based systems. Management Functions Session recording and logging All maintenance sessions to Linux Server based Firewalls can be fully recorded, to enable the post analysis of all operations performed during any intervention. All accesses performed through the IP-KVM system to the Server's console will be recorded and stored as video-clip files on the HyperServer subsystem called HyperRelay. When Serial-based or LAN-based connection services are used to access the Firewall, depending on the implementation of the connection, either a history file of all the commands and answers passed through the HyperNode will be recorded or a Video type recording will be saved for future checking or re-play. Full information on the technician performing the connection is also recorded: Technician's Name, Date and Time of the start of the intervention, Date and Time of the end of the intervention, the IP address used by the technician during the connection are fully available for subsequent analysis. Proactive monitoring To monitor the functionality of a Linux based firewall is possible to use SNMP monitoring over LAN. HyperManage allows the possibility to centrally upload a MIB file describing traps generated by the firewall. It is then possible to configure the HyperNode to react upon reception of traps containing specific OIDs (Object Identifier) and generate specific alarms on the HyperManage platform. In this case, the firewall will be configured to send SNMP traps to his guardian HyperNode; the traps will then be locally analyzed and, if they match the ones programmed on HyperManage, the HyperNode will generate an alarm that will be forwarded to HyperManage for the programmed handling. Central storage of configuration/backup files HyperManage can be configured to allow the centralized storage of the configuration files of a managed firewall as a backup system. This way users and technicians can upload the firewall's configuration files to the HyperManage Server. The centralized access to such files by privileged technician in order to analyze them can be very important in fault prevention. The system wide availability of the firewall configuration files will be perceived an essential feature during a fail-over procedure. Each configuration can be uploaded as a compressed file, and a comment file can be linked to each uploaded configuration. For every backup configuration uploaded, HyperManage makes sure that all user's details including date and time of the backup operation are stored in the system. |
 |