Server Management
Operational
functions
functions
Management
functions
functions
Emergency
functions
functions
Deployment
tutorial
tutorial
 |
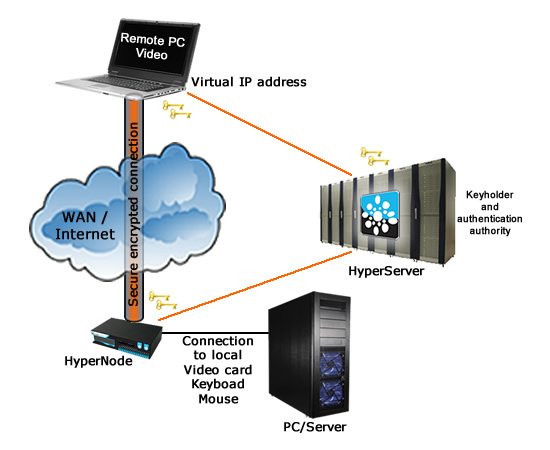 HyperManage provides Server Console Access via HyperNode IP-KVM port The IP-KVM server connection of the HyperNode allows to physically remote a server access by remoting its Keyboard, Video, and Mouse and operate them from a different remote computer. Further more the HyperNode based KVM system not only provides Server Remote Control down to the BIOS level, it also allow remote media mapping so that a block type device like a disk image physically located on the remote computer can be made available on the Controlled Server. Key advantages and enhancement delivered by HyperManage over a standard KVM system:
LAN based operational services As far as LAN based services, Servers can enjoy all the wealth of functions that are available as IP services and that can be run on top of the HyperManage generated secure hardware based VPN. SSH, Telnet, RDP, VNC and so on. Operational Conditions: All the LAN based operations are dependent on the Server's LAN card being operational and can be made independent from the primary LAN access availability by connecting the HyperNode to an alternative LAN access or an Out of Band access realised by inserting a USB 3G pen into the InfraNode. Server Console Access via Serial Console port This connection is realised by connecting the physical serial port of the HyperNode to a Server's Serial Console Port especially useful on Linux based servers where can be important not to be dependent on potential LAN malfunctions or misconfigurations in order to make ssh or telnet based management sessions. This connection remains operational independently from the Local Area Network status. As far as the HyperNode has a route to reach the HyperServer either via the primary WAN/LAN link or via a Secondary Network Connection or an Out of Band Connection like a 3G based link created by inserting a USB 3G Key into the HyperNode, then the Server's serial console port will remain remotely accessible. Remote Power Control The Power Control Function will also remain functional in such a condition and this will allow give a could boot to the Server if required. KVM function remains active during the Server boot process. Automatic Login feature The login procedure to the Server, like all login procedures to all managed devices, is centrally managed by the HyperServer via the HyperManage auto-login function. This leaves the credentials to login on the different devices known only to the HyperServer. When the access of a technician to a device or to the entire system has to be suspended it is suspended by centrally disabling his RSA-key and no other security precautions are needed because technicians do not have knowledge of any credentials necessary to login onto the different devices. |
 |